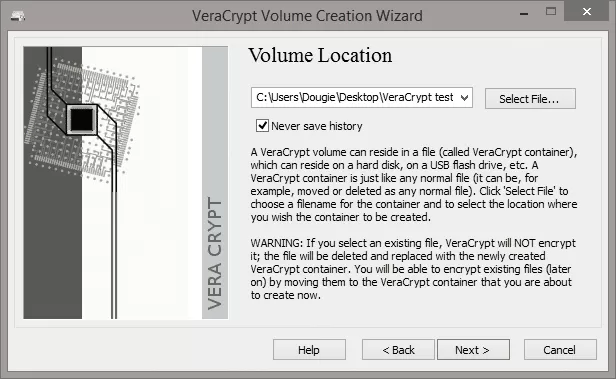
If you want to delete a VeraCrypt volume, you must first unlock it. You can do this using the Unlock VeraCrypt Volume tool. After you have unlocked the volume, you must format it using the appropriate format. You can use either FAT or exFAT.
You can then move or rename the volume. You can also choose a new password to protect the encrypted volume. Before you can format the volume, you must choose the encryption strength. Usually, VeraCrypt uses AES, the same encryption strength as the US government uses. However, you can use a different encryption strength if you need to protect home recipes.
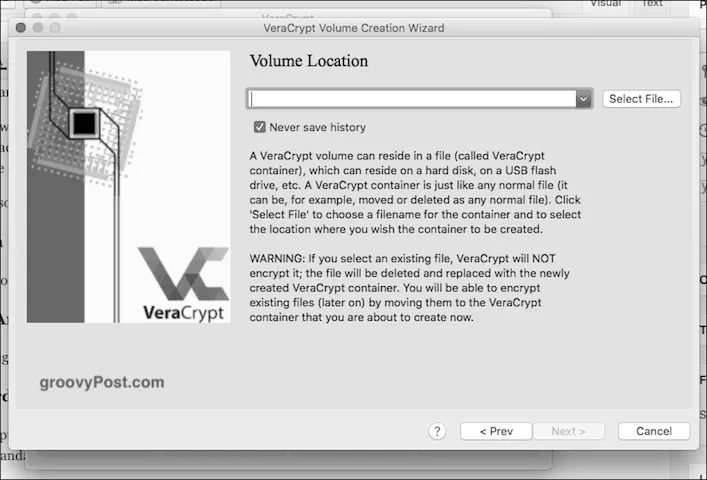
If you have installed VeraCrypt on your PC, you may have been notified that you can’t read the encrypted volume. If you want to view the contents of your encrypted volume, you can use the Volume Manager. You can even select the files you wish to access.
You can also recover deleted files by using the VeraCrypt recovery tool. To do this, you must first mount your encrypted disk. Then, you need to enter the password. Afterwards, you can recover lost files that have been deleted after formatting. Fortunately, VeraCrypt can recover your lost files, even after formatting your hard drive. However, it is important to mount the encrypted disk before scanning it.
The VeraCrypt volume is a special type of encrypted file container. This encrypted volume can be stored in any location. However, it doesn’t affect the plausible deniability of the virtual machine. The files stored in the volume are stored in a file with a PIM or keyfile.
In some cases, you may not be able to uninstall VeraCrypt, so you must remove it properly. If you’re having trouble removing the software, you can import the VeraCrypt logs into a tool called Revo Uninstaller Pro. Afterwards, you should be able to see the progress of the uninstall.
VeraCrypt can be used on macOS, Windows, and Linux systems. In fact, it supports LUKS in Linux and Tails in the MacOS environment. You should choose a compatible file system if you want to access your data in different environments. By selecting a cross-compatibility option, you can protect your data against unauthorized access.